Onboarding configuration guide#
This document will walk you through the configuration necessary to get up and running with Argus PBI for your organization. If you need any help, please do not hesitate to contact support and we can answer any questions or walk through these steps on a call with you. These permission steps follow Microsoft's guidance for using the Power BI Admin APIs. This process needs the following roles to complete:
- Azure AD administrator
- Power BI or Office 365 administrator
1. Create an Azure App Registration#
This Azure App Registration will act as the service principal that the Argus PBI backend uses to authenticate when interacting with the Power BI APIs in your tenant. This is the entity which will have permissions to call the Power BI APIs in your tenant.
- Navigate to the Azure portal.
- Search for 'app registrations' and click on the item of the same name.
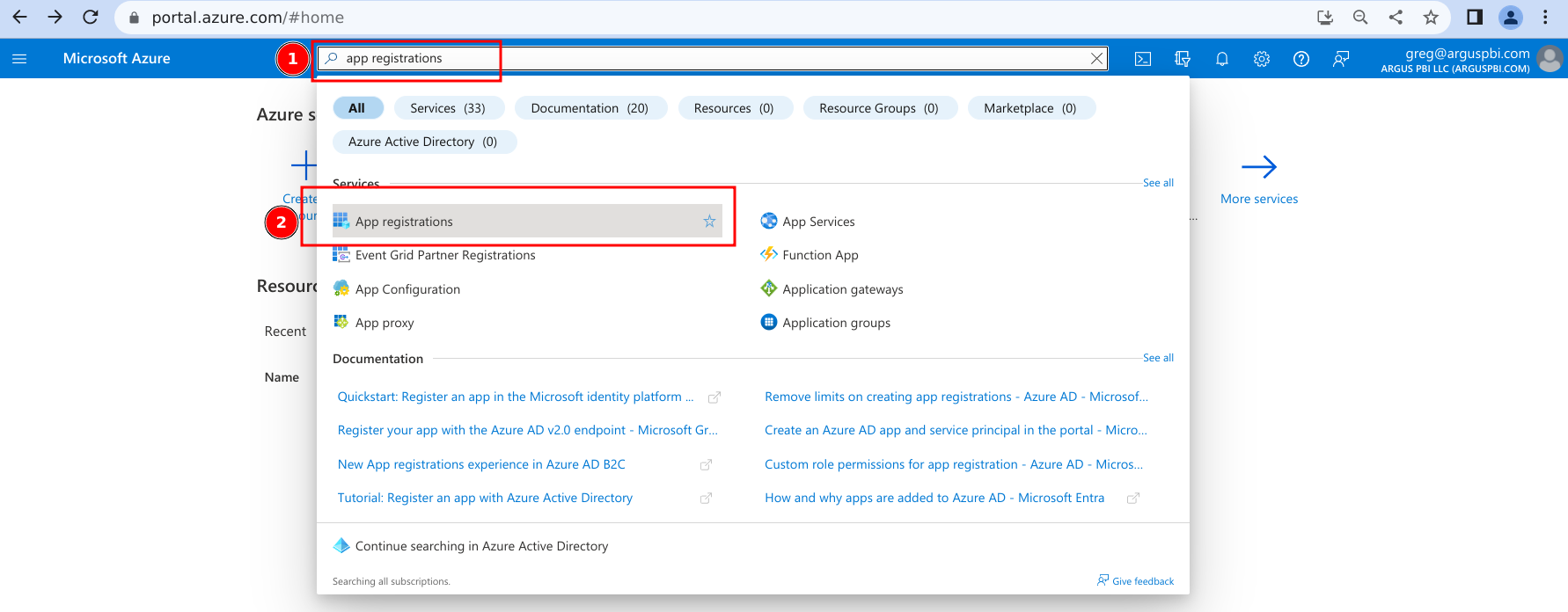
- Select '+ New registration'.
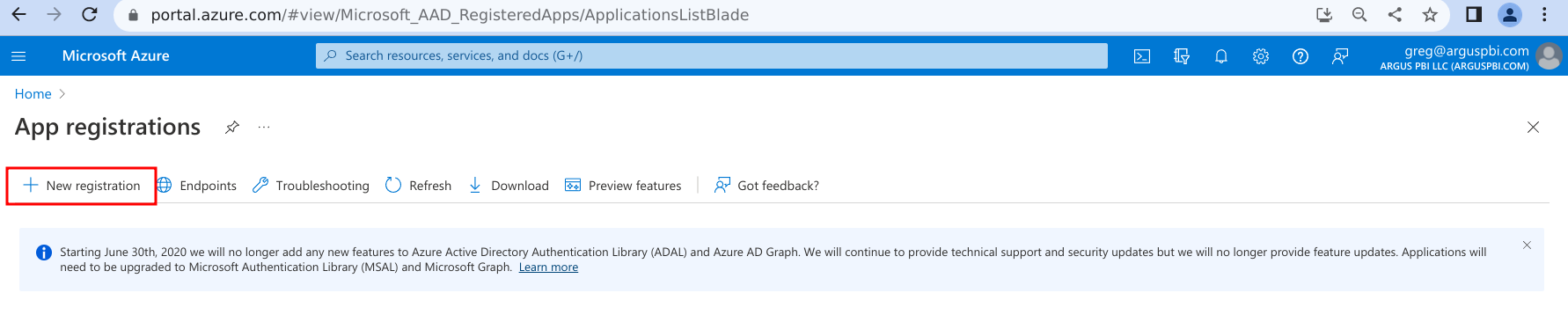
- Provide a name for the app registration -- this value can follow any naming convention you like and is for your own internal management.
- Leave supported account types at default.
- Set type of 'Web' and leave the redirect URI empty.
- Click 'Register'.
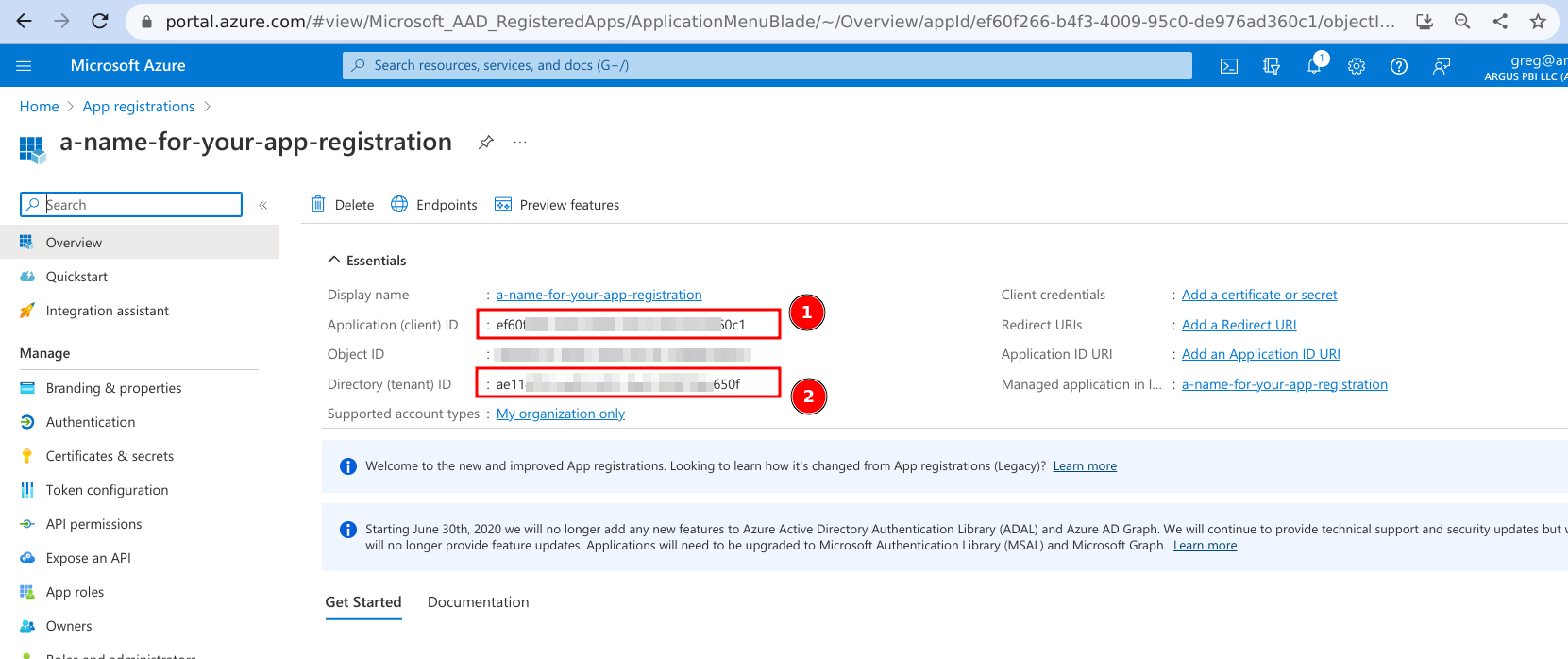
- Capture the Application and Directory IDs.
You will need to provide these to us.
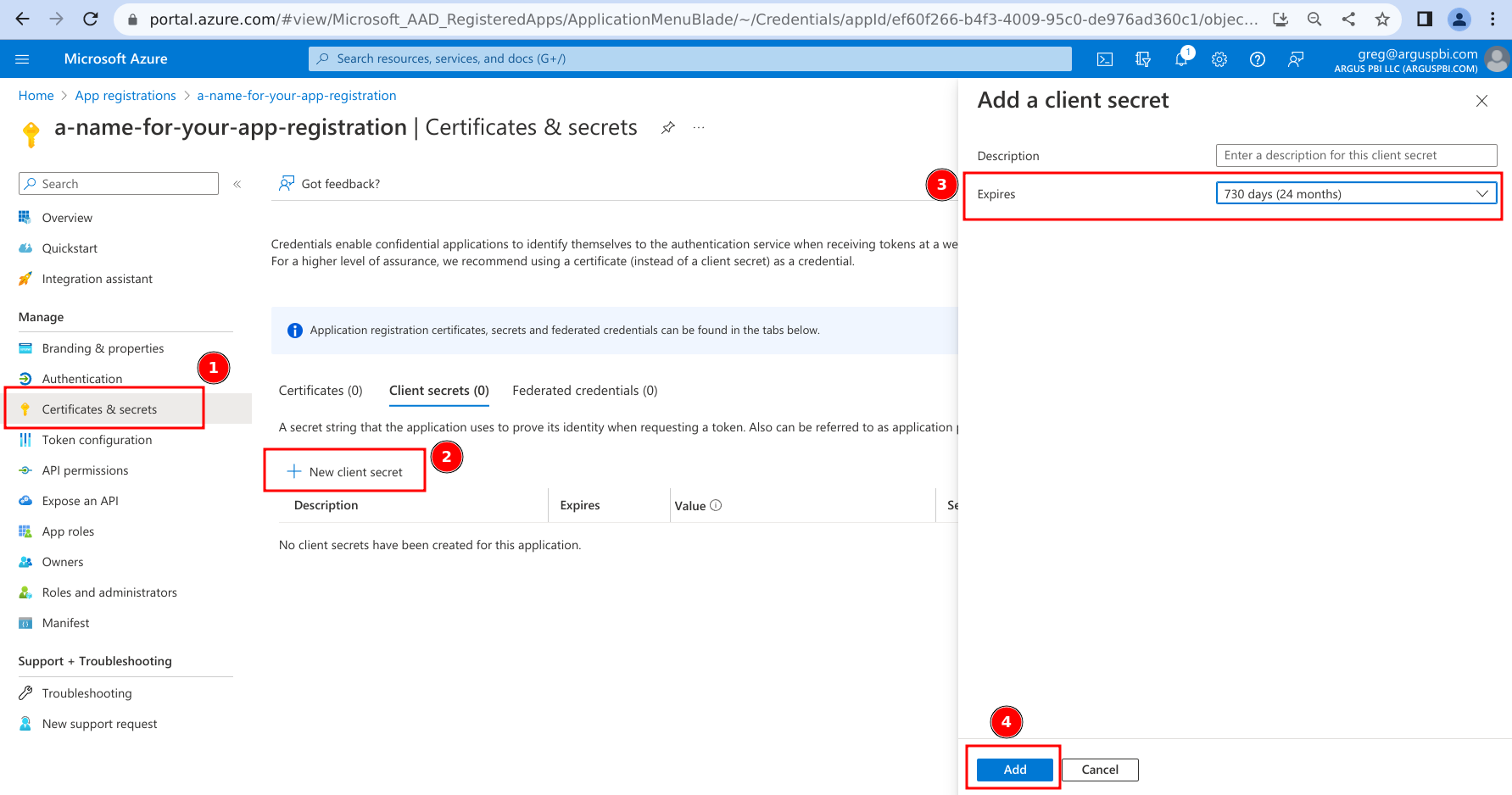
- Navigate to 'Certificates & secrets'.
- Click on '+ New client secret'.
- Alter 'Expires' to be '730 days (24 months)'.
- Optionally, you can provide a description here which will be displayed in the Azure portal, but is not used anywhere else.
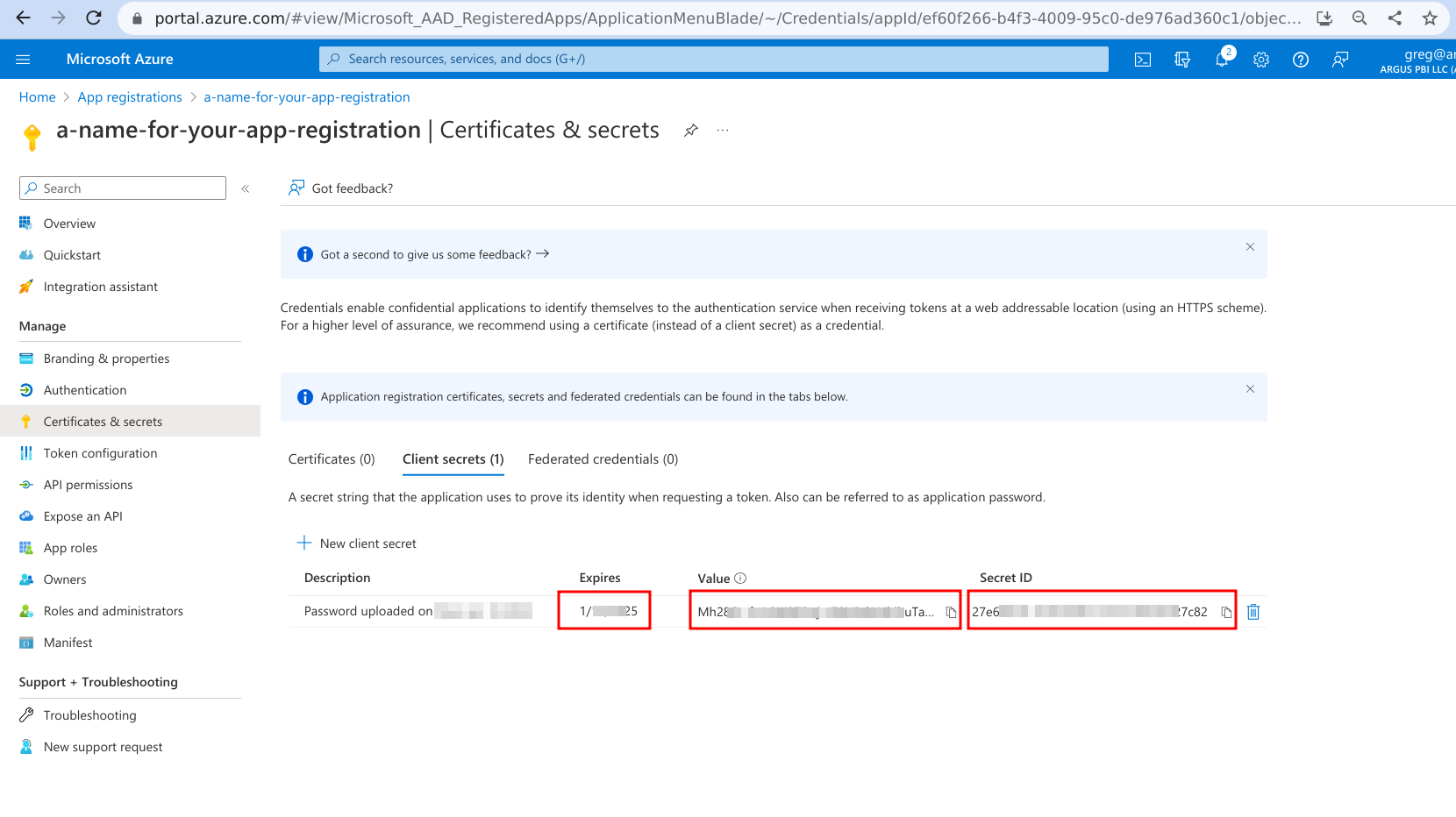
- Optionally, you can provide a description here which will be displayed in the Azure portal, but is not used anywhere else.
- Capture the fields 'Expires', 'Value', and 'Secret ID'. You will need to provide these to us.
Note that the 'Value' will not be visible after you refresh your browser or navigate to another page.
The 'Value' is equivalent to a password, so keep it secret and keep it safe.
In the next section we describe how you can securely share this information with us.
You can use the small copy icons next to 'Value' and 'Secret ID' to copy these values if they do not display in full on your browser.
2. Share App Registration details with Argus PBI#
Contact Argus PBI support to share the App Registration details. These are the items from steps 8 and 11 above. Do not email the values directly, as these are credentials which allow all API access that Argus PBI will use. When you send the email, simply let us know that you have created the app registration and we will provide a link where you can securely provide the App Registration details. The only person who will be able to access this link will be the person who sends the email, so please have the person who created the app registration and captured its details email us.
3. Create a Security Group and add the App Registration as a member#
Most customers prefer to create a Security Group specifically for this purpose, but you may use any existing Security Group if you prefer. Any members of this security group will be given permissions to call the Power BI Admin APIs in the next configuration step. If you are using a pre-existing Security Group, please go to the section, Use an existing Security Group to add the App Registration created above to the security group.
- Navigate to the Azure portal.
- Search for 'groups' and click on the item of the same name.
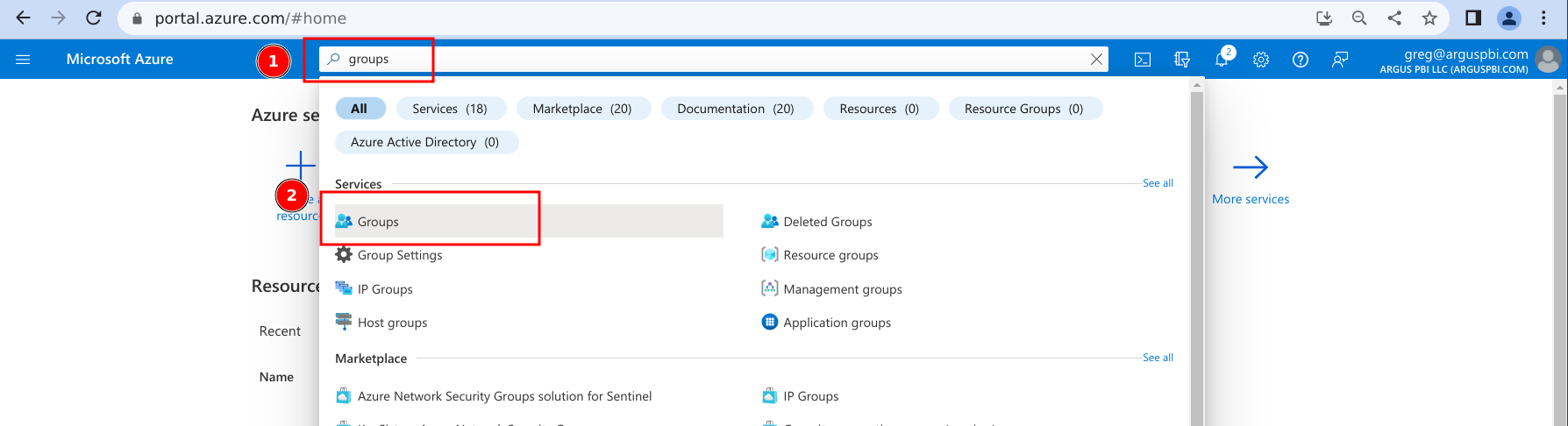
- Click on 'New group'.
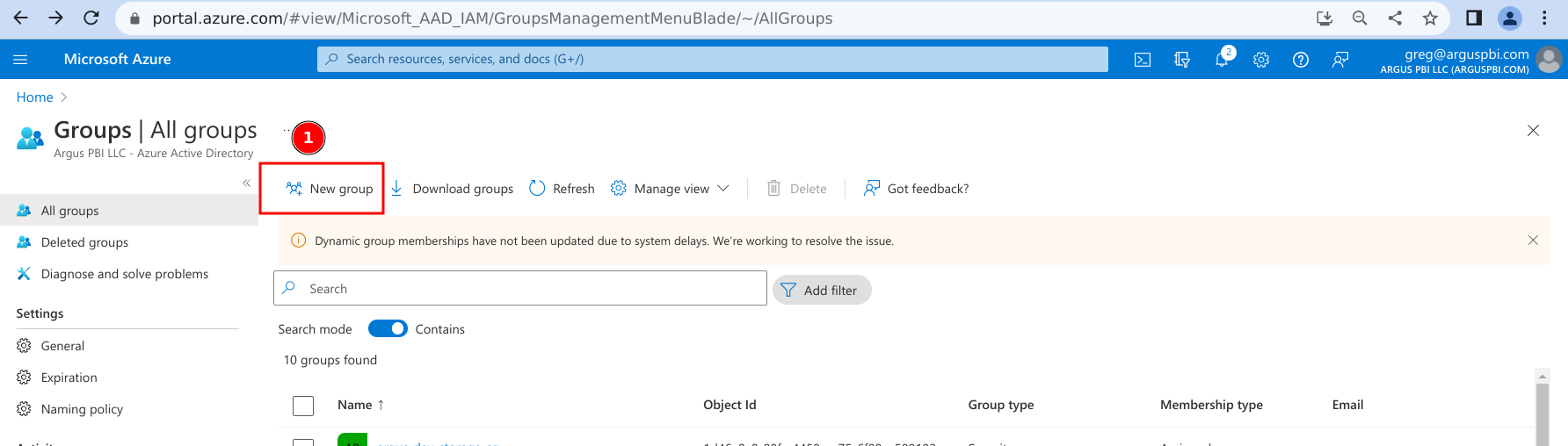
- Provide a name for the security group.
- Add an owner to the security group:
- Click on 'No owners selected'
- Search for the user name you want to be the owner
- Click on the user's name
- Click on 'Select'
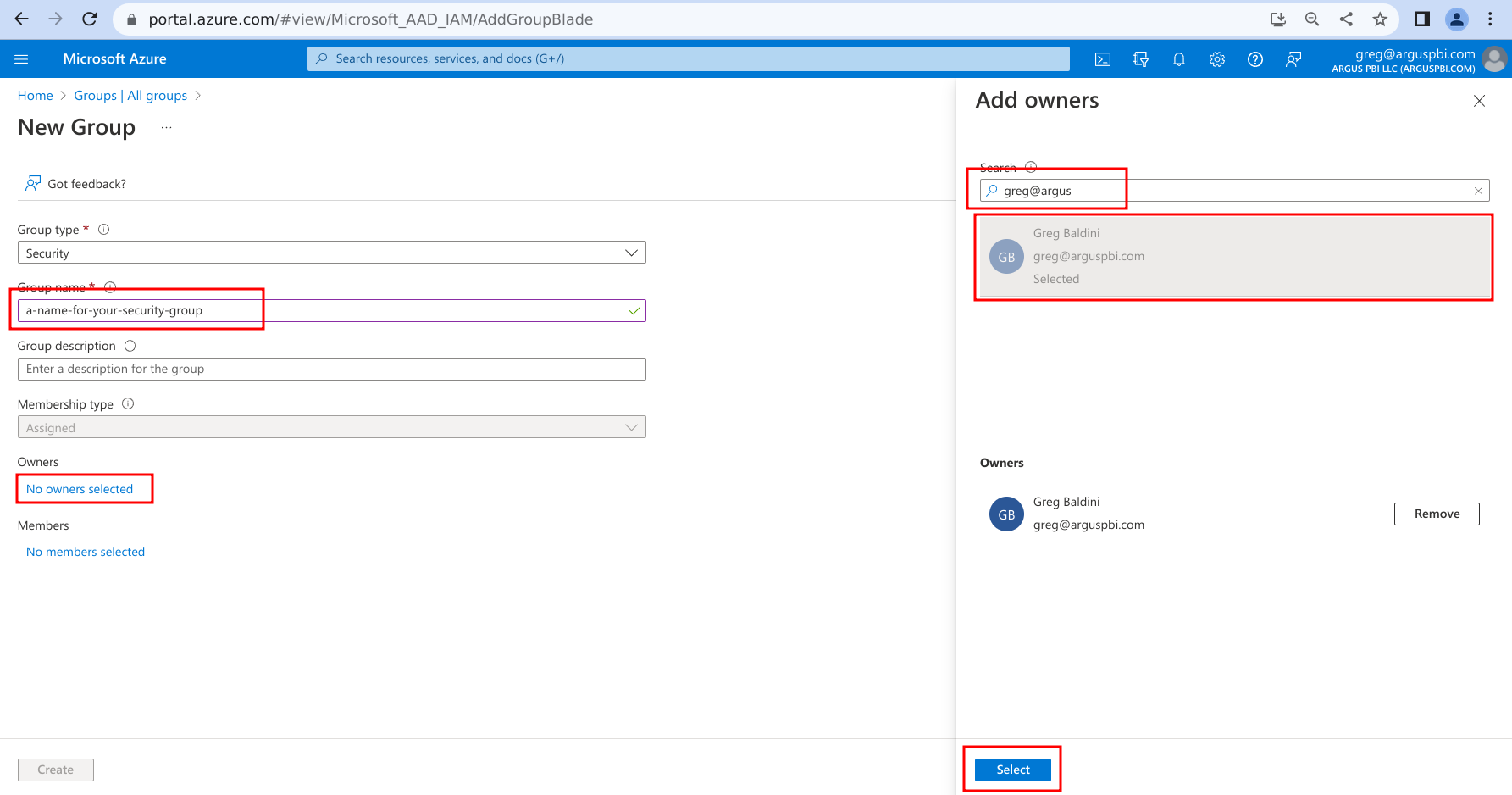
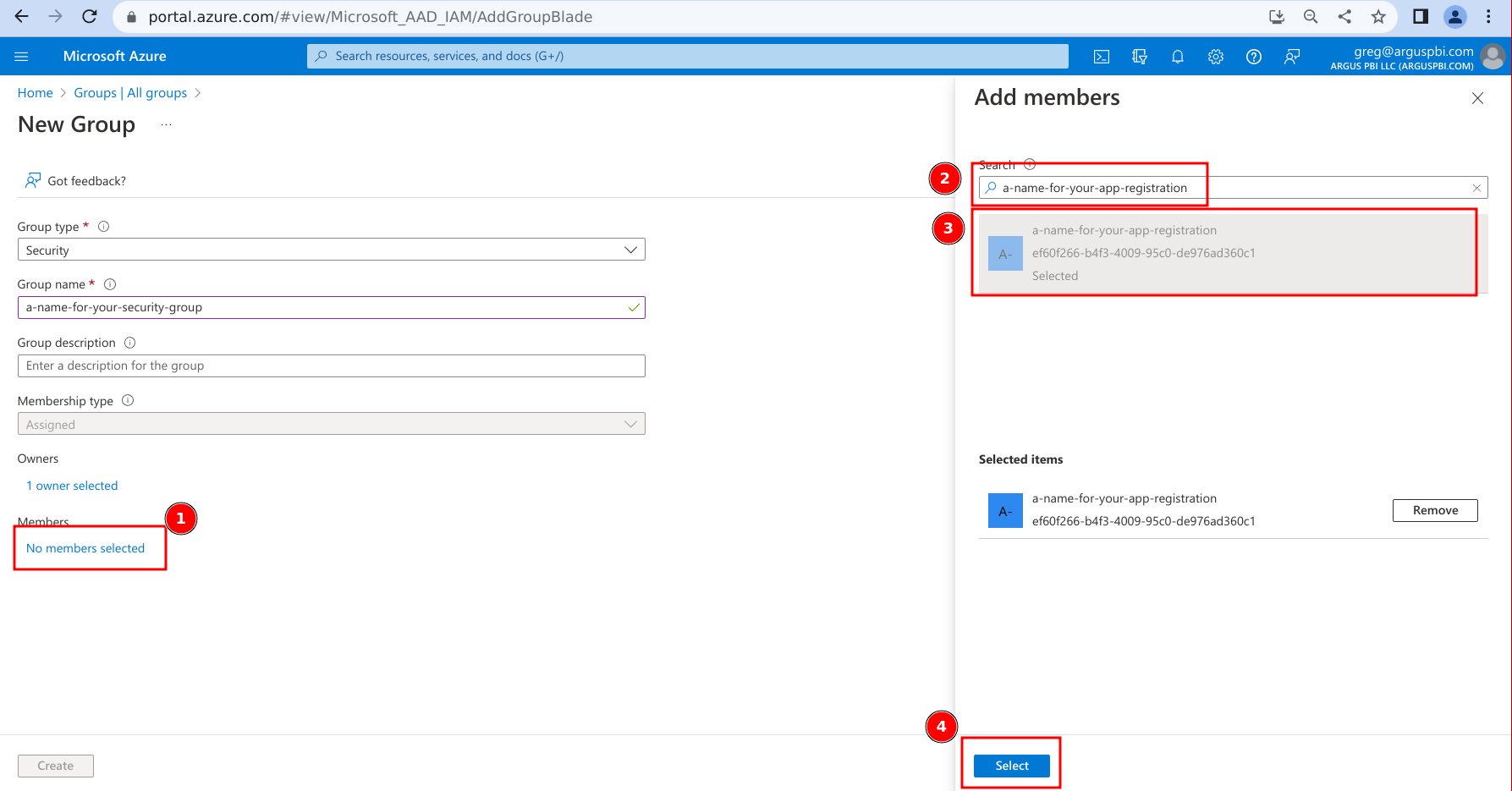
- Add the App Registration as a member of the group:
- Click on 'No members selected'
- Search for the App Registration name you created above
- Click on the App Registration's name
- Click on 'Select'
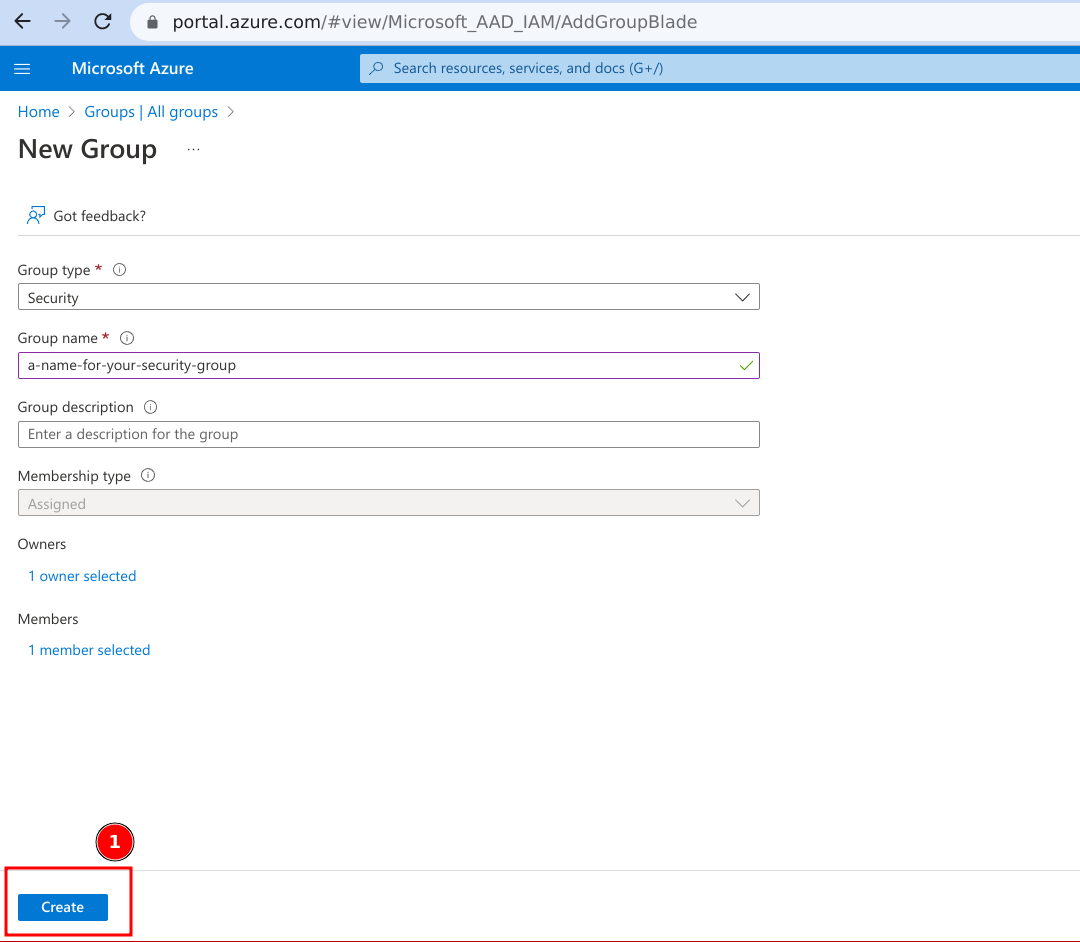
- Click on 'Create'.
Use an existing Security Group#
If you would prefer to use an existing Security Group, you can. Note that in the next section, the Security Group will be given permissions to use Power BI's Admin APIs.
- Navigate to the Azure portal.
- Search for 'groups' and click on the item of the same name.

- Search for the Security Group you would like to use and click on its name.
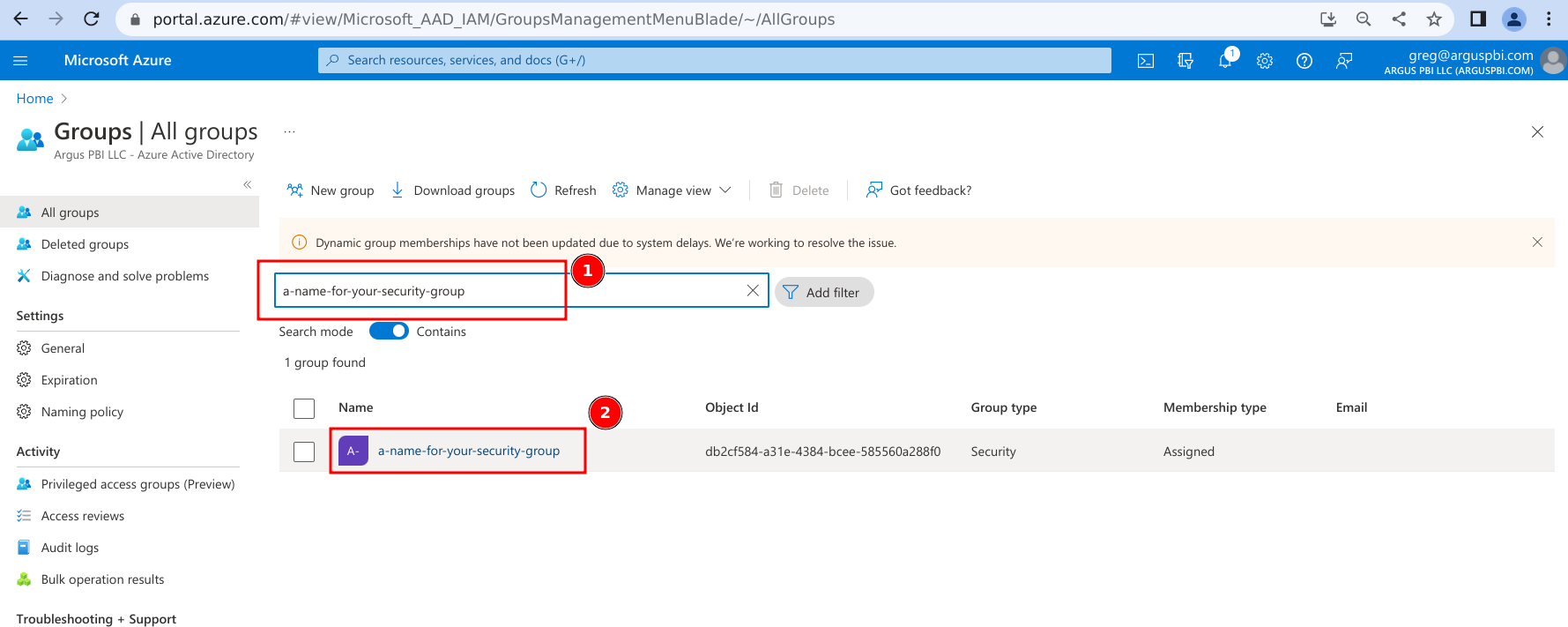
- Click on 'Members'.
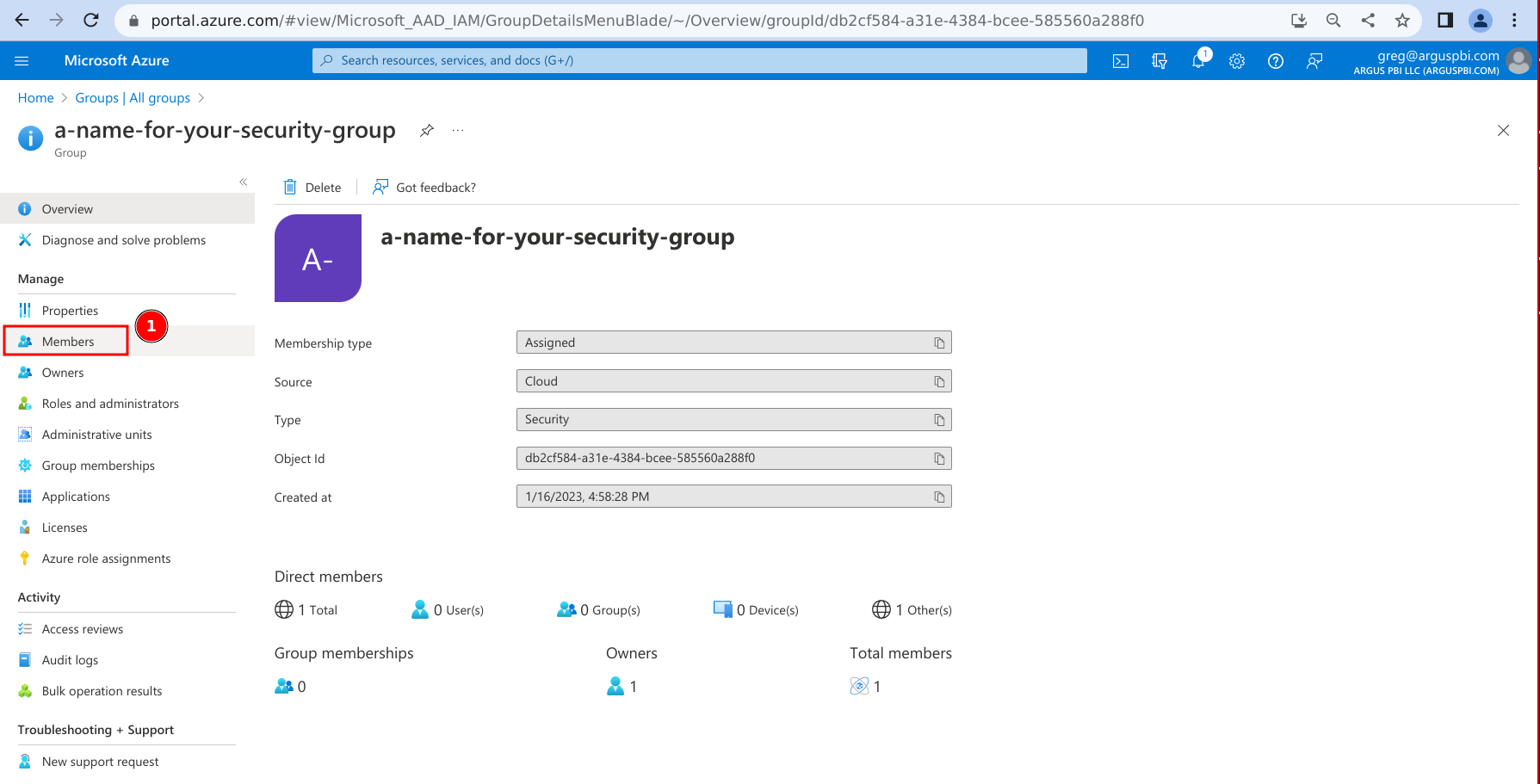
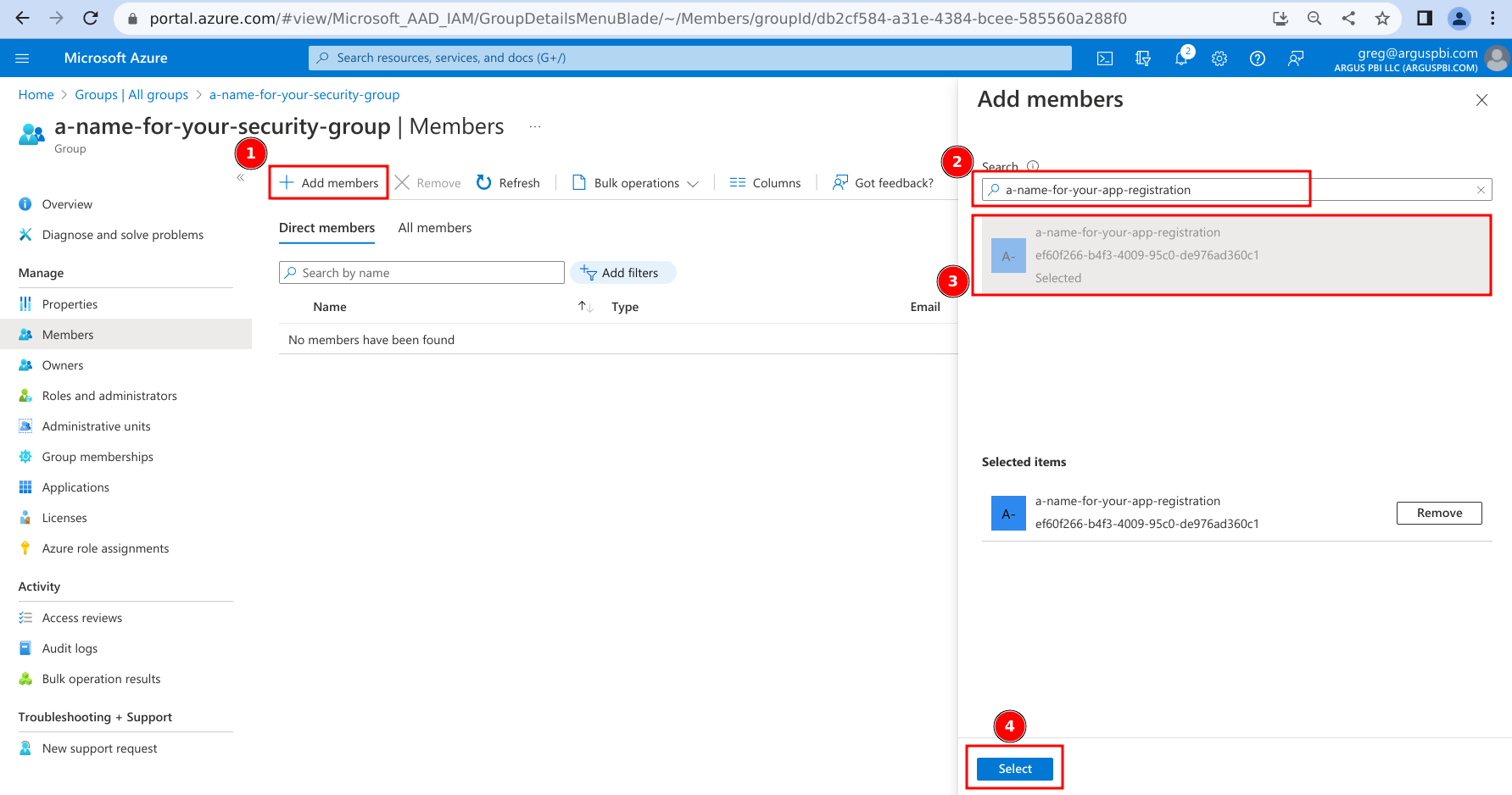
- Add your App Registration as a member of the Security Group:
- Click 'Add members'.
- Search for your App Registration's name.
- Click on your App Registration.
- Click on 'Select'
4. Configure Power BI Admin permissions#
In this section, we configure permissions for the App Registration (via the Security Group it belongs to) to be able to call Power BI's Admin APIs.
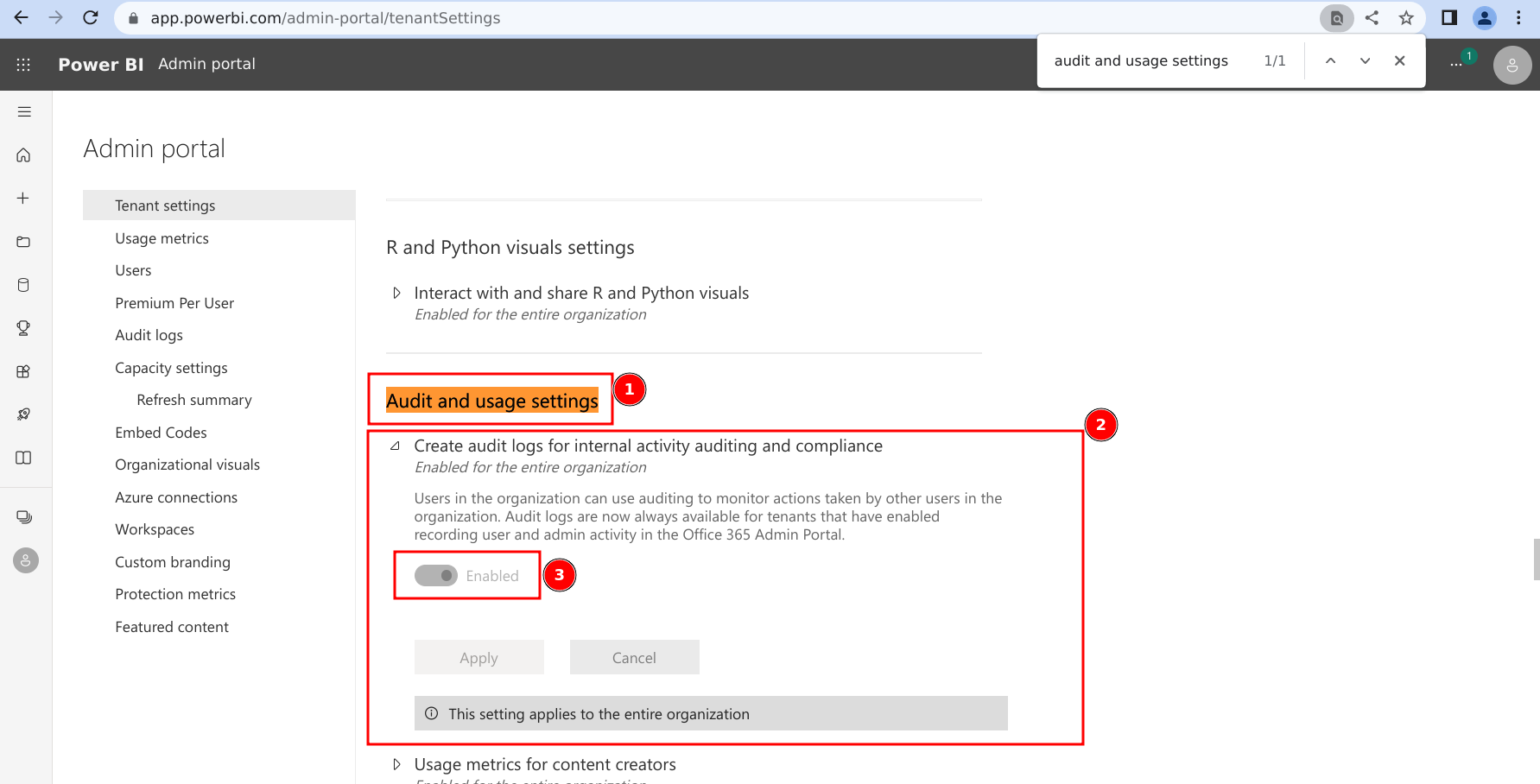
- Navigate to the Power BI Admin portal.
- Scroll (or search in the page) until you find 'Audit and usage settings'.
- Expand the subsection for 'Create audit logs for internal activity auditing and compliance'.
- Ensure that the setting is toggled to Enabled.
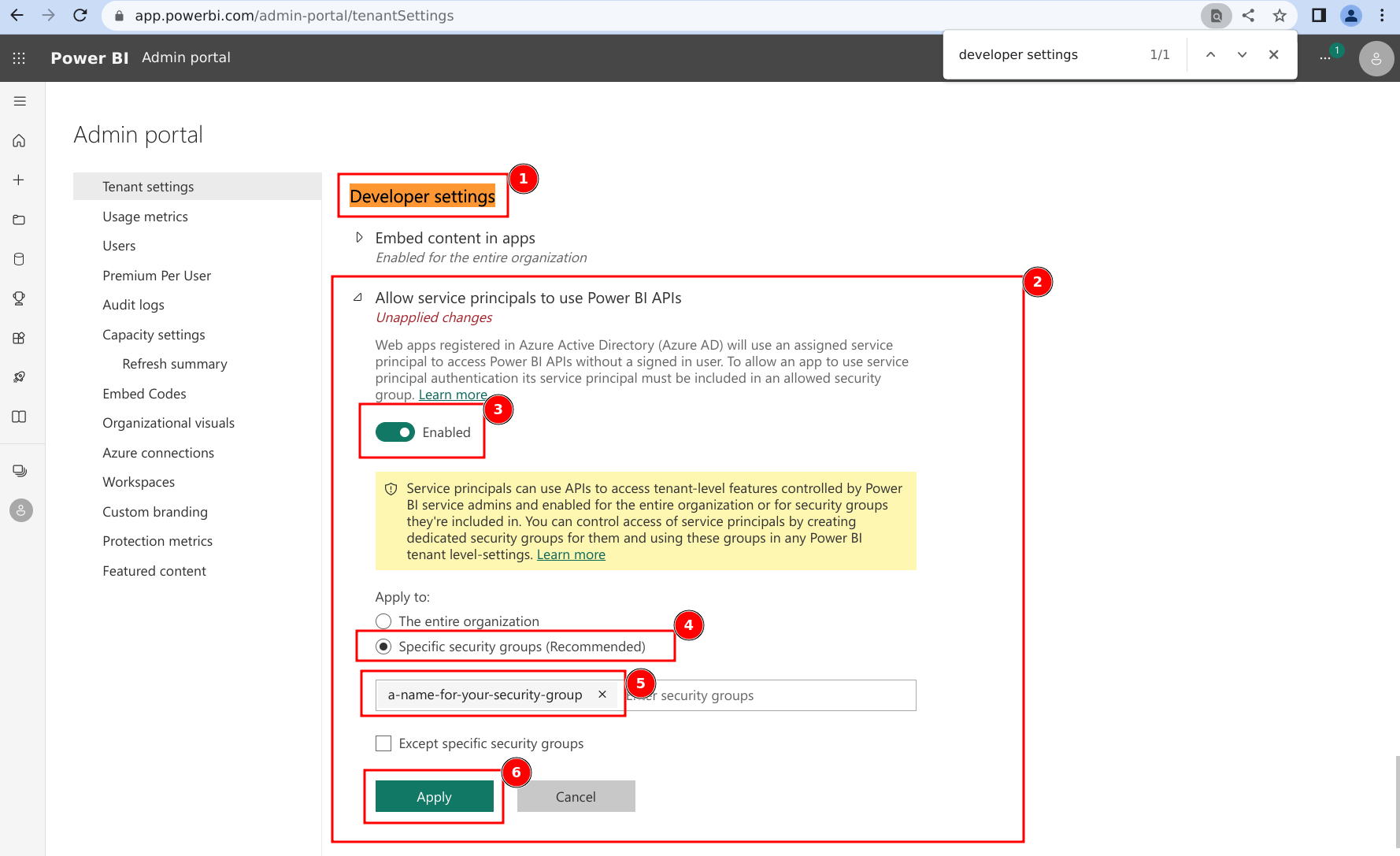
- Scroll (or search in the page) until you find 'Developer settings' (it should be directly below 'Audit and usage settings' from above).
- Expand the subsection for 'Allow service principals to use Power BI APIs.
- Ensure that the setting is toggled to Enabled.
- Click on the radio selection for 'Specific security groups (Recommended)
- Add the Security Group configured above to the allowed list.
- Click on 'Apply'.
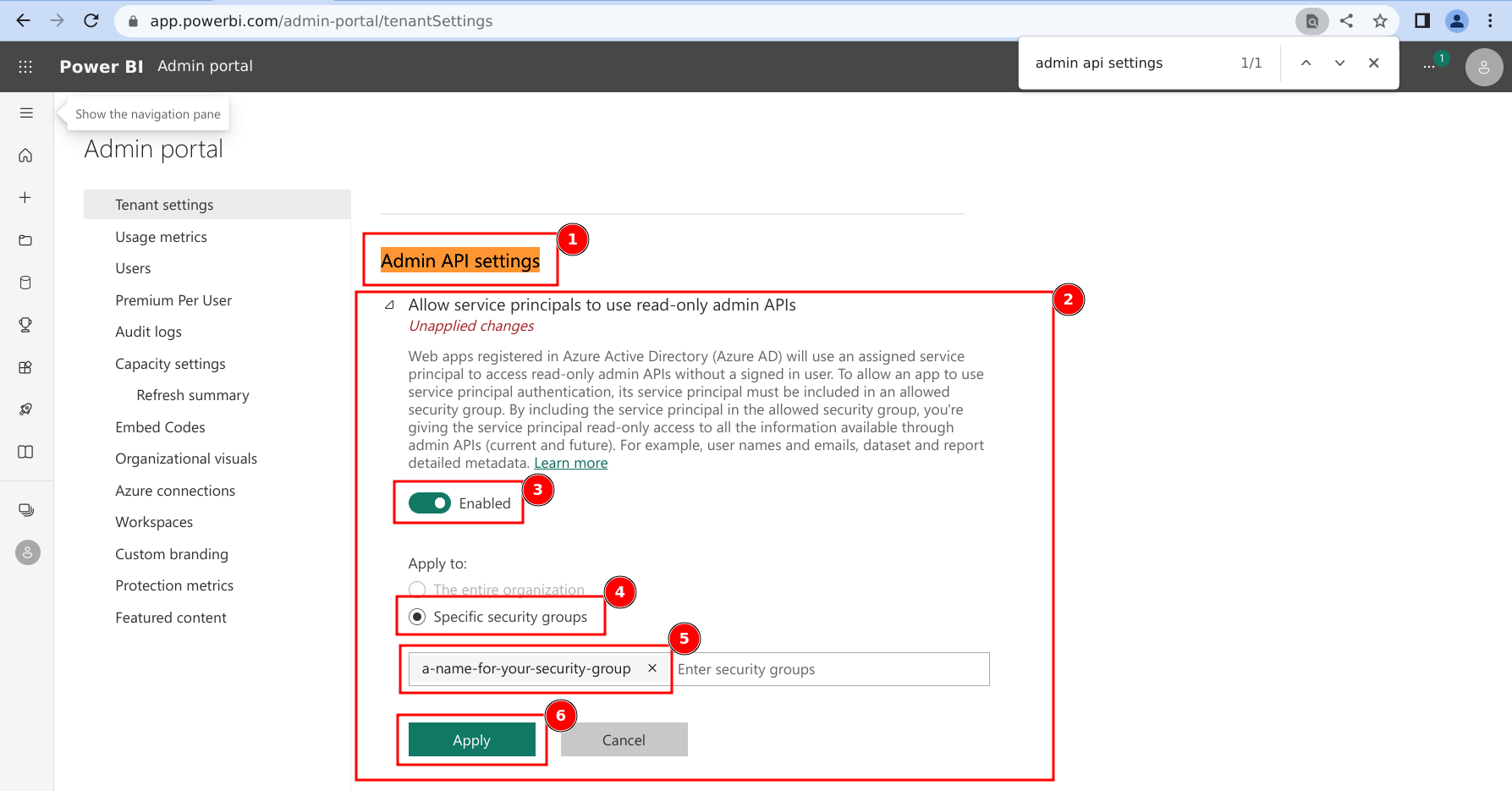
- Scroll (or search in the page) until you find 'Admin API settings' (it should be directly below 'Developer settings'from above).
- Expand the subsection for 'Allow service principals to use read-only admin APIs'.
- Ensure the setting is toggled to Enabled.
- Click on the radio selection for 'Specific security groups'
- Add the Security Group configured above to the allowed list.
- Click on 'Apply'.
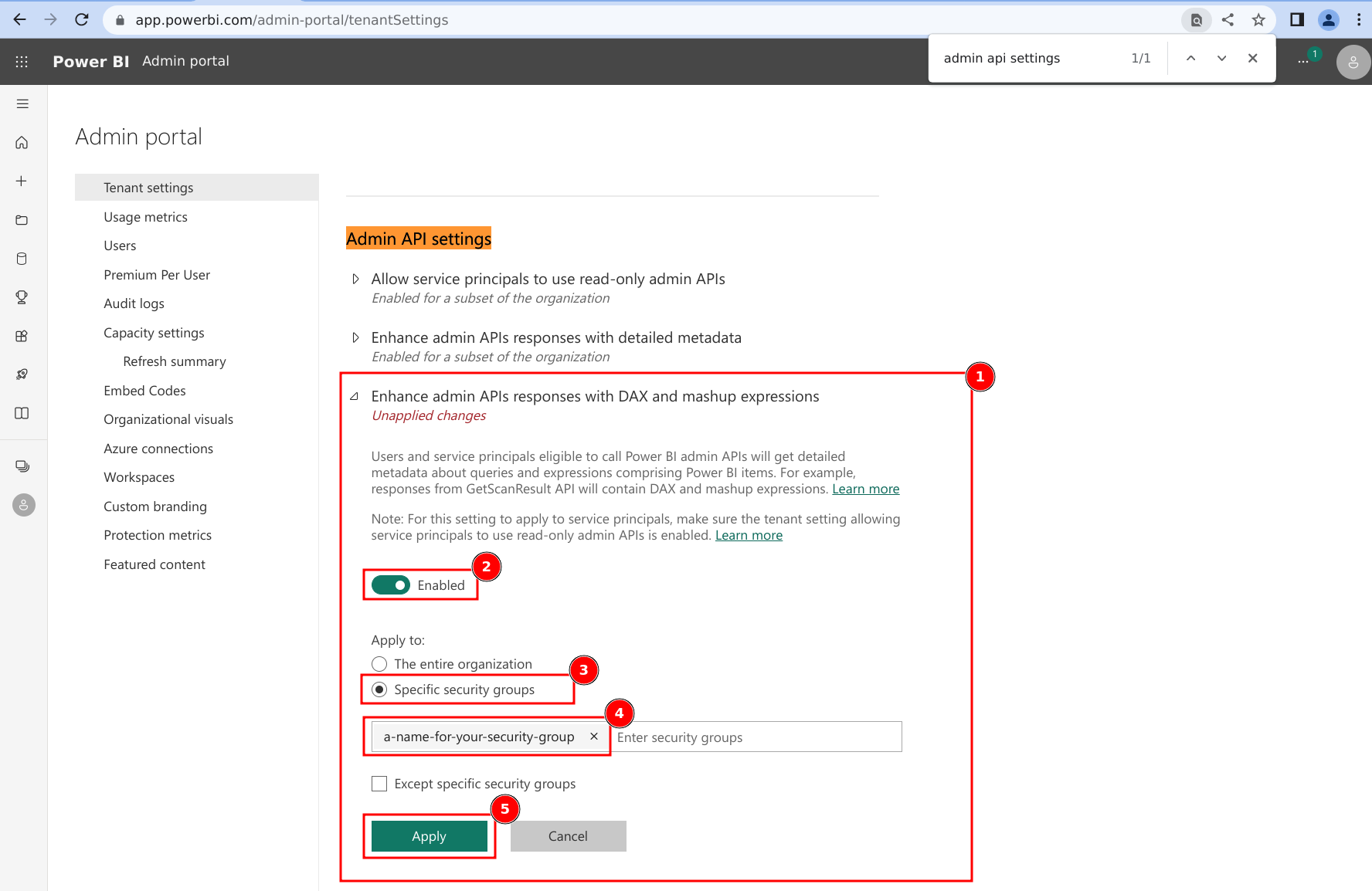
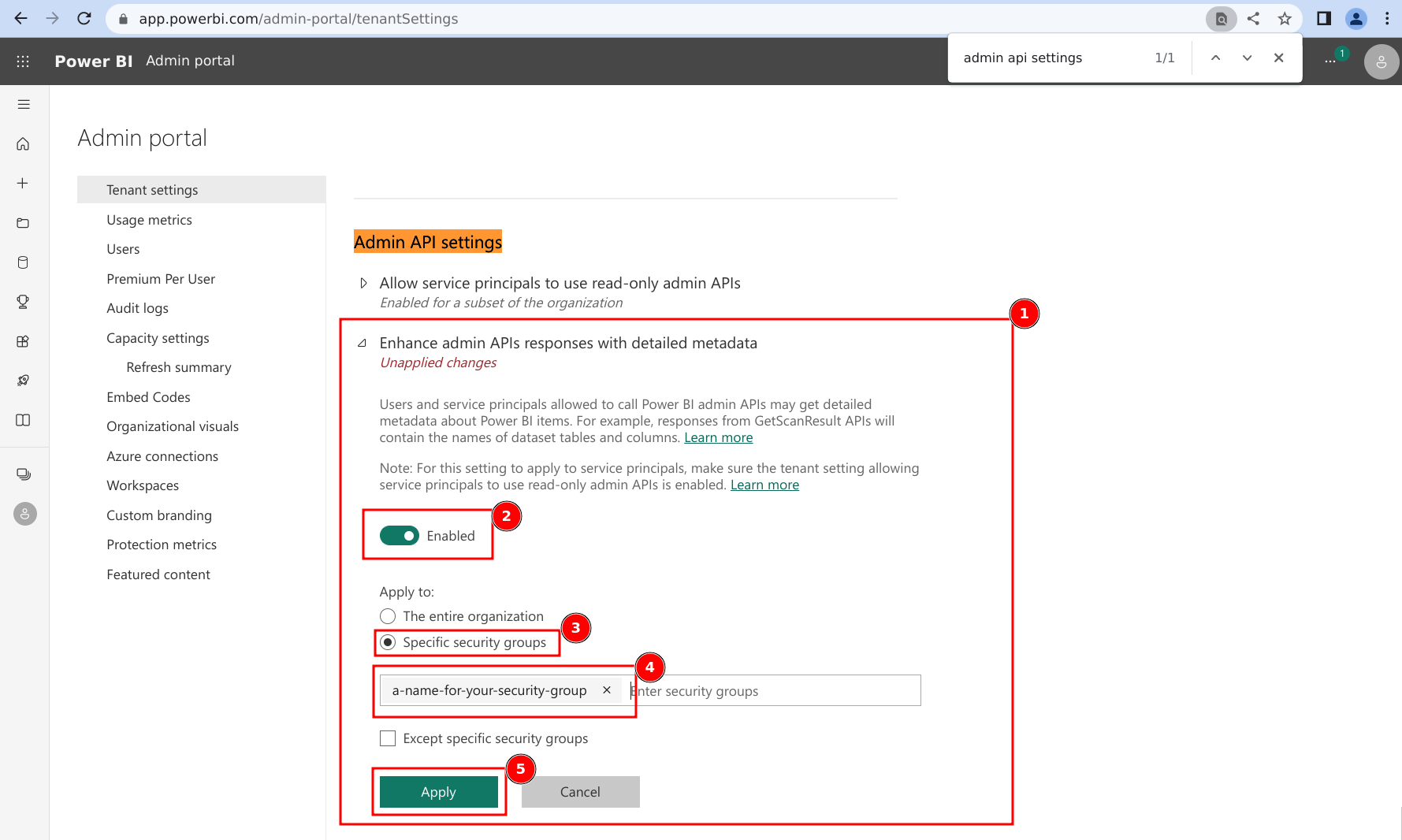
- Expand the subsection for 'Enhance admin APIs responses with detailed metadata'.
- Ensure the setting is toggled to Enabled.
- Click on the radio selection for 'Specific security groups'
- Add the Security Group configured above to the allowed list.
- Click on 'Apply'.
- Expand the subsection for 'Enhance admin APIs responses with DAX and mashup expressions'.
- Ensure the setting is toggled to Enabled.
- Click on the radio selection for 'Specific security groups'
- Add the Security Group configured above to the allowed list.
- Click on 'Apply'.